Security Vulnerability
Vulnerability is a circumstance that given the realization of a threat could expedite harm to people or damage to objects. If the threat involves human intent, the vulnerability is a weakness that can be exploited by the perpetrator (for example weakly guarded entrances to an object).
In the context of security, this means that the absence of measures increases the risk of harm or damages. For example, certain public spaces of interest can be considered soft targets. This means that crowded public places including the metro, shopping centres, sports stadiums, bars, restaurants, clubs and commercial sidewalks, are easily accessible to the public and an easy target for terrorists to do great harm. These spaces inherently carry a risk of potentially far-reaching harm, or put in other words, are potentially vulnerable.
Given the focus on human intent, the concept of security vulnerability can be seen more suitable for use by security organisations (such as LEAs) or event planners whereas safety vulnerability, on the other hand, is a concept more suitable for the use by urban planners.
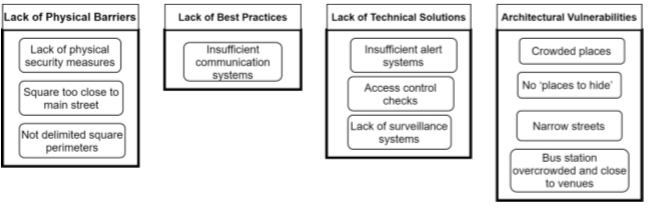
The following figure shows examples of missing measures that increase the security vulnerability of a location. These examples are derived from the EU PRoTECT project.
Threat types
Threats can be categorised in a number of threat types. Vulnerabilities and their mitigation are generally associated with one or more threat types. The following threat types have been used in EU projects:
- Fire arms attack - small calibre pistol or semi/full-automatic rifle;
- Sharp object attack - knifes, machete, other sharp and blunt objects;
- Vehicle attack - use of vehicle as a weapon by ramming large crowds;
- Improvised Explosive Device (IED) - left/concealed in objects or goods (based on home-made or commercial explosives);
- Person-Born Improvised Explosive Device (PBIED) - explosives concealed on a person (suicide or carrier);
- Unmanned Aerial Vehicle Improvised Explosive Device (UAVIED) - explosives delivered by a remote-controlled airborne device;
- Vehicle-Borne Improvised Explosive Devise (VBIED) - explosives concealed inside a vehicle (or its cargo);
- Chemical attack - threat object concealed in goods or carried items (e.g. canister or UAV dispensed);
- Biological attack - threat object concealed in goods or carried items (e.g. canister or UAV dispensed);
- Radiological attack - threat object concealed in goods or carried items (e.g. canister or UAV dispensed).
Identification of vulnerabilities
In the EU PRoTECT project a method was used to identify and assess vulnerabilities.
Examples of vulnerabilities and possible solutions
In ProTECT research, a number of vulnerabilities due to absence of measures were identified and in the context of the research, a number of possible (preferred) solutions were put forward. The following table contains a number of these pairs of vulnerabilities with possible solutions. Please note that these are examples as found in the specific context of the PRoTECT research.
Vulnerabilities and possible solutions
| Vulnerabilities | Possible Solutions |
| Lack of physical barriers (lack of physical security measures; square to close to main street; not delimited square perimeter)
|
Physical barriers proposed solutions: 1. Metallic fences 2. Bollards 3. Panic room
|
| Lack of best practices (insufficient communication systems)
|
Best practices proposed solution: 1. Community awareness training 2. Victim support approaches after attack 3. OSINT technologies (threat detection tools) 4. Risk assessment tools and techniques 5. Simulation, training, and gaming tools 6. Solutions for terrorist crisis management 7. Fast transfer information practices 8. Organisation based on GIS systems
|
| Lack of technical solutions (insufficient alert systems; access control checks; lack of surveillance systems)
|
Technological proposed solution: 1. CCTV to record people and vehicles 2. Anomaly detection systems 3. Fire detectors 4. Automatic Sprinklers 5. Millimetre wave scanner 6. System optimum travel information (PSOI) 7. Audio analytics systems 8. Signal jamming devices for drones 9. WiFi and communication systems
|
| Architectural vulnerabilities (crowded places, no 'places to hide'; narrow streets; bus station overcrowded and close to venues)
|
Architectural proposed solution: 1. Environmentally integrated solutions 2. Light exit pathways 3. Motion sensor lights 4. Architectural modification and improvements
|